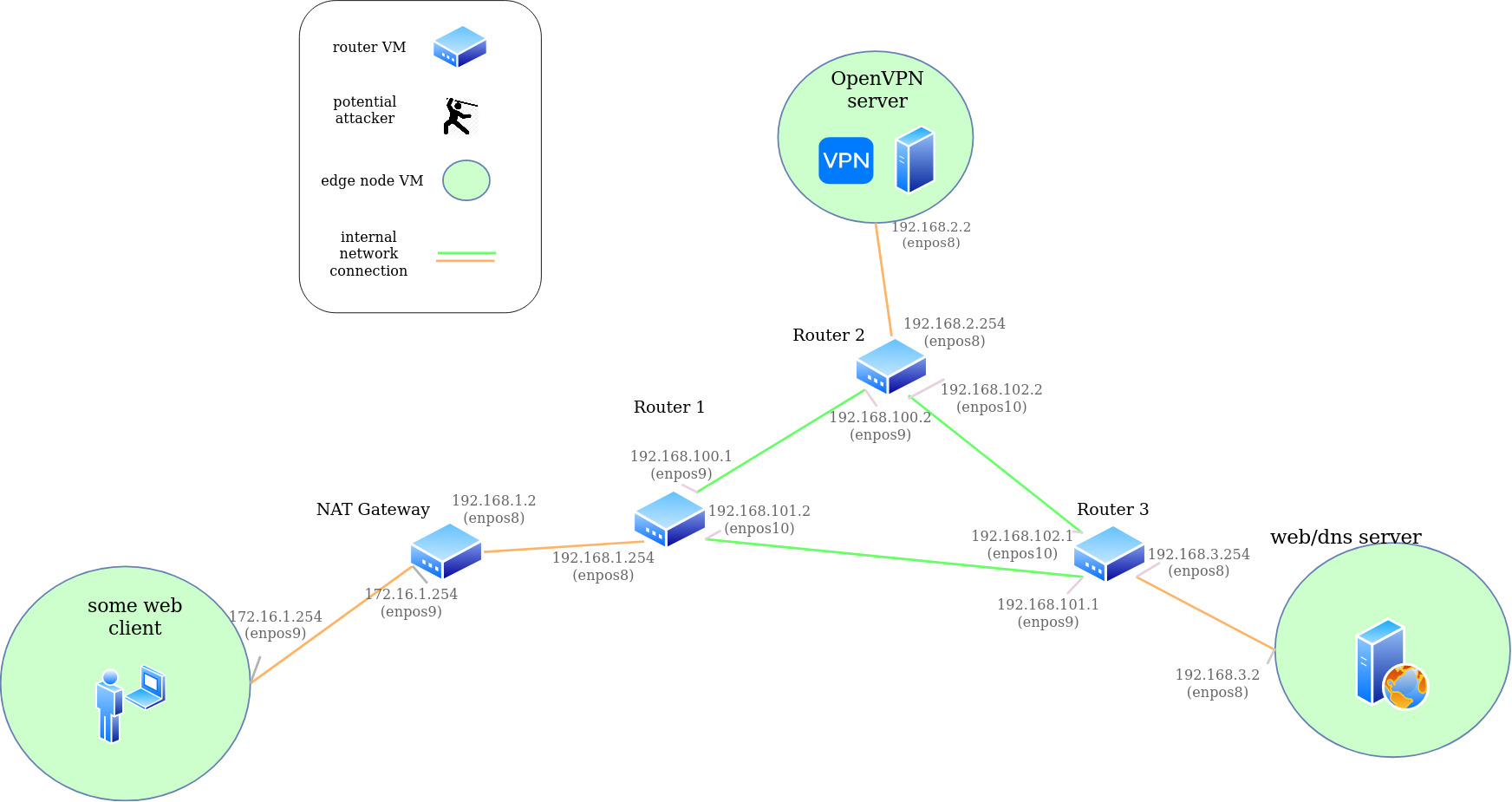
virt-lab
VM lab environment for doing network stuff
Requirements
- Virtualbox (5.2 or older)
- Vagrant 2.2.x
Setup base virtual network
- Start all 6 VMs (3 routers and 3 edge nodes):
./boot_all.sh - Go do something else cause its gonna take a while..
- (Optional) ssh to some machine:
- ssh by port:
ssh -l vagrant localhost -p 22111 - ssh with vagrant:
cd edgers/vpn-server/ && vagrant sshorcd <path-to-vagrantfile> && vagrant ssh
- Restart all the machines to make network changes take effect:
./stop_all.shthen./start_all.sh - Build VPN server and add VPN client config file to client node:
cd virt-lab/configs; ./configure_vpn.sh
Connect client to VPN server
- Ssh to the client VM:
cd virt-lab/edgers/client && vagrant ssh - Connect to the local vpn server:
./connect.sh
Client-Side Attack
Configure client side attack environment
- Navigate to configuration folder:
cd virt-lab/configs - Run setup script to build gateway attacker node:
./setup_cliside_env.sh
Test client side attack
- ssh to victim client VM (base host):
cd virt-lab/edgers/client && vagrant ssh - Connect client to VPN (in client vm):
./connect.sh - Open another shell to ssh to web server node (base host):
cd virt-lab/edgers/web-server && vagrant ssh - Open another shell to ssh to gateway attacker node (base host):
cd virt-lab/routers/gateway && vagrant ssh - On web-server vm, open a netcat connection for the client to connect to:
nc -l 8080 - On the client vm, connect to the web server:
nc 192.168.3.2 8080 -p 40404 - On the attacker vm, navigate to the attack folder:
cd vpn-attacks/client-side-attack - Rebuild all the attack scripts (attacker):
./rebuild_all.sh - Navigate to full attack folder (attacker):
cd complete_attack - Start full attack script (attacker):
./attack.sh - Wait for script to infer private tun IP, port in use, exact sequence number, and in-window ack number needed to inject TCP
Server-Side Attack
Configure server side attack environment
- Navigate to configuration folder:
cd virt-lab/configs - Run setup script to build gateway attacker node:
./setup_servside_env.sh.sh
Test server side DNS attack
- ssh to victim client VM (base host):
cd virt-lab/edgers/client && vagrant ssh - Connect client to VPN (in client vm):
./connect.sh - Open another shell to ssh to router1 attacker node (base host):
cd virt-lab/routers/router1 && vagrant ssh - On the attack router vm navigate to dns inject folder:
cd vpn-attacks/server-side-attack/dns-sside/full_scan/ - Compile full attack script (attacker):
make - Issue DNS lookup from client vm:
nslookup test.com 192.168.3.2 - Start inject script from attacker node:
./inject_test.sh
Teardown
- Stop all the VMs:
./stop_all.sh - Destroii all VMs in our path:
./destroy_all.sh